Nuovi Use Cases e articoli
Link alle novità
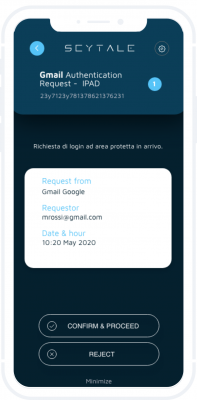
Signchain Authchain
PSD2 Compliant Strong Authentication
Un metodo di autenticazione basato sull'uso congiunto di due canali e due o più fattori, con l’aggiunta della trasparenza e immutabillità della firma blockchain.
Contatta il nostro sales team